Using password-based authentication for the Teams Connector CVI application
This topic explains how to use password-based authentication with the Teams Connector. It covers:
- Deploying a new (first time) Teams Connector with password-based authentication
- Upgrading or redeploying a Teams Connector that is still using password-based authentication
Certificate-based authentication (CBA) is now the default method to authenticate the Teams Connector CVI application towards MS Graph. You can still use the previous password-based authentication method, but we plan to deprecate it in a future release, thus we recommend using CBA for new installations, or migrating to CBA as soon as practicable when upgrading existing deployments.
Deploying a new (first time) Teams Connector with password-based authentication
You can follow most of the standard steps for installing the Teams Connector via CBA. However, there are some variations to the installation script and the post-deploy process as described below.
Remember to run your standard variable initialization script first (the variable script is the same for either authentication method), before running this installation script.
The installation script for password-based authentication is provided below, and should be used instead of the one provided with the main installation instructions. This script uses a password to authenticate the Teams Connector CVI application towards MS Graph.
This script applies to software version 39. If you are using an earlier version you should refer to our previous documentation.
- Standard deployment
- High-security deployment (typically Azure GCC High / US Government)
# Ensure the correct script and software combination is being used
try {$PxConnMajorVersion = (Get-Content .\version.json -ErrorAction Stop | Out-String | ConvertFrom-Json).major} catch {Write-Warning "Can't find version.json file. Make sure you run the installation script from the folder into which you extracted the files from the Teams Connector ZIP"}
if ($PxConnMajorVersion -ne "39"){Write-Warning "The Connector version (extracted ZIP files) and this deployment script version do not match. Connector version = $PxConnMajorVersion. Deployment script version = 39"}
# Connect to Microsoft Graph, Azure Resource Manager account and import Pexip CVI module
# Microsoft Graph commands
# Connect to Microsoft Graph
# If AAD/365 admin account is not the same as Azure Resource Manager admin account,
# the next section is to be run by the AAD admin.
#
# IMPORTANT: The output of IDs/credentials here must be saved as it will be required later
#
# IMPORTANT - DEPRECATION NOTICE:
# A certificate-based authentication process for the CVI application is the default for the Teams Connector from v34
# The password authentication method will be deprecated in a future release
# Set execution policy for the current PowerShell process, when prompted type A (Yes to All)
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process
# The Unblock-File cmdlet lets you run PowerShell script files that were downloaded from the internet.
# By default, these files are blocked to protect the computer from untrusted files.
Get-ChildItem -Recurse | Unblock-File
# Import the PexTeamsCviApplication PowerShell module
Import-Module .\PexTeamsCviApplication.psm1
# Import Az Powershell modules
Import-PexAzurePowershellModules -ErrorAction Stop
# Import Microsoft.Graph Powershell modules
Import-PexMicrosoftGraphPowershellModules -ErrorAction Stop
# Connect to Azure with an authenticated account for use with Azure Resource Manager (in same window to reuse variables)
Connect-AzAccount
# Connect to Graph
Connect-PexTeamsMsGraph
# Create Pexip CVI Application
# Create App
$App = New-PexTeamsCviApplication -AppDisplayName "$($PxBaseConnName)TeamsConn" -Confirm:$false
$AppId = $App.AppId
# Create App Password
$AppPassword = ($App | New-PexTeamsCviApplicationPasswordCredential -DisplayName "$($PxBaseConnName)TeamsConn").SecretText
Write-Host
Write-Host
Write-Host "`n----------------------------------------`n"
Write-Host
Write-Host "### CVI App ID and credentials MUST be saved in the redeploy script ###"
Write-Host
Write-Host "### IMPORTANT - DEPRECATION NOTICE:"
Write-Host "### A certificate-based authentication process for the CVI app is the default for the Teams Connector from v34"
Write-Host "### The password authentication method will be deprecated in a future release"
Write-Host
Write-Host "`$AppId = `"$($AppId)`""
Write-Host "`$AppPassword = `"$($AppPassword)`""
Write-Host
Write-Host "`n----------------------------------------`n"
Write-Host
Write-Host
# Change context to the Pexip Subscription and set the app credentials
Set-AzContext -SubscriptionId $PxSubscriptionId
$AppSecurePassword = ConvertTo-SecureString -AsPlainText $AppPassword -Force
# Azure Bot for the CVI AppID
# Create bot (must be globally unique, and only needs to be created once - in any of your regions)
Register-PexTeamsCviApplicationBot -SubscriptionId $PxSubscriptionId -ResourceGroupName $PxBotResourceGroupName -BotName "$($PxBaseConnName)-TeamsBot" -AppId $AppId -Confirm:$false -Tag $tags
# Deploy Pexip Teams Connector admin consent web page
$AdminConsentUrl = Publish-PexTeamsAdminConsentWebSite -SubscriptionId $PxSubscriptionId -ResourceGroupName $PxBotResourceGroupName -PxBaseConnName $PxBaseConnName -AppId $AppId -SourceAddressPrefixes $PxConsentSourceAddressPrefixes -Confirm:$false -Tag $tags
# Virtual Machine Scale Set (VMSS) creation
# Provide credentials to be used as local user/password for Pexip Teams Connector VMs
# Create a password (using the initialization script variables) for the Windows VM
$PxWinAdminSecurePassword = ConvertTo-SecureString -AsPlainText $PxWinAdminPassword -Force
$PxWinAdminCred = New-Object System.Management.Automation.PSCredential -ArgumentList $PxWinAdminUser,$PxWinAdminSecurePassword
# Optionally if you did not want to specify the password as a variable, use Get-Credential
# $PxWinAdminCred = Get-Credential
# Deploy the Teams Connector VMs
# this step can take up to 30 minutes to complete
.\create_vmss_deployment.ps1 -SubscriptionId $PxSubscriptionId -AzureVmSize $PxAzureVmSize -ResourceGroupName $PxTeamsConnResourceGroupName -VmssName "$($PxBaseConnName)$($PxVmssRegion)" -VMAdminCredential $PxWinAdminCred -PfxPath $PxPfxCertFileName -TeamsConnectorFqdn $PxTeamsConnFqdn -PexipFqdns $PxNodeFqdns -instanceCount $PxTeamsConnInstanceCount -AppId $AppId -AppPassword $AppSecurePassword -StaticResourcesResourceGroupName $PxTeamsConnStaticResourceGroupName -IncidentReporting $PxTeamsConnIncidentReporting -RdpSourceAddressPrefixes $PxMgmtSrcAddrPrefixes -PexipSourceAddressPrefixes $PxNodesSourceAddressPrefixes -WupdScheduledInstallDay $PxWupdScheduledInstallDay -WupdScheduledInstallTime $PxWupdScheduledInstallTime -WupdActiveHoursStart $PxWupdActiveHoursStart -WupdActiveHoursEnd $PxWupdActiveHoursEnd -CustomerUsageAttribution $PxCustomerUsageAttribution -UseAzureHybridBenefit $PxUseAzureHybridBenefit -Tag $tags -TeamsConnectorApiApplicationId $TeamsConnectorApiApplicationId -FunctionsDedicatedHostingPlan $FunctionsDedicatedHostingPlan -EventHubSourceAddressPrefixes $EventHubSourceAddressPrefixes -VnetIntegration $VnetIntegration -PexipConfiguredConnectorFqdn $PexipConfiguredConnectorFqdn -PexipOutboundFqdn $PexipOutboundFqdn -ExistingVNETResourceId $PxExistingVNETResourceId -UsePrivateRouting $PxUsePrivateRouting
# supply the PFX certificate file password when prompted
# Please enter the password for the PFX certificate '.\xxxxxxxx.pfx': ***************
# Generating the next steps summary (this assumes you are connected to Microsoft Graph and with an authenticated account for use with Azure Resource Manager)
#
# Setting subscription
Set-AzContext -SubscriptionId $PxSubscriptionId
# Getting IP configurations
if ($PxUsePrivateRouting) {
$LB = Get-AzLoadBalancer -ResourceGroupName $PxTeamsConnResourceGroupName
$ExtLB = $LB | Where-Object { $_.Name.EndsWith("-LB") }
$IntLB = $LB | Where-Object { $_.Name.EndsWith("-INTLB") }
$LBExtIPID = $ExtLB.FrontendIpConfigurations[0].PublicIpAddress.id
$LBIntIP = $IntLB.FrontendIpConfigurations[0].PrivateIpAddress
$PublicIPAddresses = Get-AzPublicIpAddress -ResourceGroupName $PxTeamsConnStaticResourceGroupName
$ConnectorPublicIP = $PublicIPAddresses | Where-Object Id -eq $LBExtIPID
$publicIpAddress = $ConnectorPublicIP[0].IpAddress
$privateIpAddress = $LBIntIP
} else {
$LB = (Get-AzLoadBalancer -ResourceGroupName $PxTeamsConnResourceGroupName)[0]
$LBPublicIPID = $LB.FrontendIpConfigurations[0].PublicIpAddress.id
$PublicIPAddresses = Get-AzPublicIpAddress -ResourceGroupName $PxTeamsConnStaticResourceGroupName
$ConnectorPublicIP = $PublicIPAddresses | Where-Object Id -eq $LBPublicIPID
$publicIpAddress = $ConnectorPublicIP[0].IpAddress
}
# Getting connection string for the newly deployed Event hub
$eventHub = (Get-AzResource -ResourceGroupName $PxTeamsConnStaticResourceGroupName -ResourceType Microsoft.EventHub/namespaces)[0]
$eventHubKey = Get-AzEventHubKey -Name "pexip_teams_connector_access" -NamespaceName $eventHub.Name -ResourceGroupName $eventHub.ResourceGroupName
# Printing next steps
Write-Host
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host "When the Teams Connector is deployed, you have to create a DNS A record for your hostname,"
Write-Host "then the Office 365 admin must consent for the CVI App Id to join Teams Meetings"
Write-Host
Write-Host "1) Set up a public DNS A record for $($PxTeamsConnFqdn) pointing to the Public IP of "
Write-Host " the load balancer ($($publicIpAddress))"
Write-Host
Write-Host "2) Give consent to the CVI app. Go to: $AdminConsentUrl"
Write-Host
Write-Host " If Management Consent Source Address prefixes are defined, the administrator"
Write-Host " doing consent must come from one of these addresses (or subnets)."
Write-Host " Consent address prefixes: $($PxConsentSourceAddressPrefixes)"
Write-Host
Write-Host "3) Update the Management Node setting 'Azure Event Hub connection string' for $($PxTeamsConnFqdn) to:"
Write-Host " $($eventHubKey.PrimaryConnectionString)"
Write-Host
if ($PxUsePrivateRouting) {
Write-Host "4) Set up a private DNS A record for $($PxTeamsConnFqdn) pointing to the (private) frontend IP of "
Write-Host " the internal load balancer ($($privateIpAddress))"
Write-Host " See: https://docs.pexip.com/admin/teams_routing.htm#enabling"
}
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host# This script applies to high-security deployments (typically Azure GCC High / US Government)
# Ensure the correct script and software combination is being used
try {$PxConnMajorVersion = (Get-Content .\version.json -ErrorAction Stop | Out-String | ConvertFrom-Json).major} catch {Write-Warning "Can't find version.json file. Make sure you run the installation script from the folder into which you extracted the files from the Teams Connector ZIP"}
if ($PxConnMajorVersion -ne "39"){Write-Warning "The Connector version (extracted ZIP files) and this deployment script version do not match. Connector version = $PxConnMajorVersion. Deployment script version = 39"}
# Set VmImage variable to hold the CIS STIG image properties - STIG image is optional but typical
# In a later step in this script you can choose not to use the STIG image
$VmImage = @{
"sku" = "cis-windows-server2022-stig-gen2"
"offer" = "cis-windows-server"
"publisher" = "center-for-internet-security-inc"
"version" = "latest"}
# Connect to Microsoft Graph, Azure Resource Manager account and import Pexip CVI module
# Microsoft Graph commands
# Connect to Microsoft Graph
# If AAD/365 admin account is not the same as Azure Resource Manager admin account,
# the next section is to be run by the AAD admin.
#
# IMPORTANT: The output of IDs/credentials here must be saved as it will be required later
#
# IMPORTANT - DEPRECATION NOTICE:
# A certificate-based authentication process for the CVI application is the default for the Teams Connector from v34
# The password authentication method will be deprecated in a future release
# Set execution policy for the current PowerShell process, when prompted type A (Yes to All)
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process
# The Unblock-File cmdlet lets you run PowerShell script files that were downloaded from the internet.
# By default, these files are blocked to protect the computer from untrusted files.
Get-ChildItem -Recurse | Unblock-File
# Import the PexTeamsCviApplication PowerShell module
Import-Module .\PexTeamsCviApplication.psm1
# Import Az Powershell modules
Import-PexAzurePowershellModules -ErrorAction Stop
# Import Microsoft.Graph Powershell modules
Import-PexMicrosoftGraphPowershellModules -ErrorAction Stop
# Connect to Azure USGovernment with an authenticated account for use with Azure Resource Manager (in same window to reuse variables)
Connect-AzAccount -EnvironmentName AzureUSGovernment
# Connect to Graph
Connect-PexTeamsMsGraph
# Create Pexip CVI Application
# Create App
$App = New-PexTeamsCviApplication -AppDisplayName "$($PxBaseConnName)TeamsConn" -Confirm:$false
$AppId = $App.AppId
# Create App Password
$AppPassword = ($App | New-PexTeamsCviApplicationPasswordCredential -DisplayName "$($PxBaseConnName)TeamsConn").SecretText
Write-Host
Write-Host
Write-Host "`n----------------------------------------`n"
Write-Host
Write-Host "### CVI App ID and credentials MUST be saved in the redeploy script ###"
Write-Host
Write-Host "### IMPORTANT - DEPRECATION NOTICE:"
Write-Host "### A certificate-based authentication process for the CVI app is the default for the Teams Connector from v34"
Write-Host "### The password authentication method will be deprecated in a future release"
Write-Host
Write-Host "`$AppId = `"$($AppId)`""
Write-Host "`$AppPassword = `"$($AppPassword)`""
Write-Host
Write-Host "`n----------------------------------------`n"
Write-Host
Write-Host
# Change context to the Pexip Subscription and set the app credentials
Set-AzContext -SubscriptionId $PxSubscriptionId
$AppSecurePassword = ConvertTo-SecureString -AsPlainText $AppPassword -Force
# Azure Bot for the CVI AppID
# Create bot (must be globally unique, and only needs to be created once - in any of your regions)
Register-PexTeamsCviApplicationBot -SubscriptionId $PxSubscriptionId -ResourceGroupName $PxBotResourceGroupName -BotName "$($PxBaseConnName)-TeamsBot" -AppId $AppId -Confirm:$false -Tag $tags -TeamsEnvironmentName TeamsGCCHigh
# Deploy Pexip Teams Connector admin consent web page
$AdminConsentUrl = Publish-PexTeamsAdminConsentWebSite -SubscriptionId $PxSubscriptionId -ResourceGroupName $PxBotResourceGroupName -PxBaseConnName $PxBaseConnName -AppId $AppId -SourceAddressPrefixes $PxConsentSourceAddressPrefixes -Confirm:$false -Tag $tags
# Virtual Machine Scale Set (VMSS) creation
# Provide credentials to be used as local user/password for Pexip Teams Connector VMs
# Create a password (using the initialization script variables) for the Windows VM
$PxWinAdminSecurePassword = ConvertTo-SecureString -AsPlainText $PxWinAdminPassword -Force
$PxWinAdminCred = New-Object System.Management.Automation.PSCredential -ArgumentList $PxWinAdminUser,$PxWinAdminSecurePassword
# Optionally if you did not want to specify the password as a variable, use Get-Credential
# $PxWinAdminCred = Get-Credential
# Deploy the Teams Connector VMs
# this step can take up to 30 minutes to complete
# if you are not using a STIG image then remove the following parameter from this command: -VmImage $VmImage
.\create_vmss_deployment.ps1 -SubscriptionId $PxSubscriptionId -AzureVmSize $PxAzureVmSize -ResourceGroupName $PxTeamsConnResourceGroupName -VmssName "$($PxBaseConnName)$($PxVmssRegion)" -VMAdminCredential $PxWinAdminCred -PfxPath $PxPfxCertFileName -TeamsConnectorFqdn $PxTeamsConnFqdn -PexipFqdns $PxNodeFqdns -instanceCount $PxTeamsConnInstanceCount -AppId $AppId -AppPassword $AppSecurePassword -StaticResourcesResourceGroupName $PxTeamsConnStaticResourceGroupName -IncidentReporting $PxTeamsConnIncidentReporting -RdpSourceAddressPrefixes $PxMgmtSrcAddrPrefixes -PexipSourceAddressPrefixes $PxNodesSourceAddressPrefixes -WupdScheduledInstallDay $PxWupdScheduledInstallDay -WupdScheduledInstallTime $PxWupdScheduledInstallTime -WupdActiveHoursStart $PxWupdActiveHoursStart -WupdActiveHoursEnd $PxWupdActiveHoursEnd -CustomerUsageAttribution $PxCustomerUsageAttribution -UseAzureHybridBenefit $PxUseAzureHybridBenefit -Tag $tags -TeamsConnectorApiApplicationId $TeamsConnectorApiApplicationId -FunctionsDedicatedHostingPlan $FunctionsDedicatedHostingPlan -EventHubSourceAddressPrefixes $EventHubSourceAddressPrefixes -VnetIntegration $VnetIntegration -VmImage $VmImage -TeamsEnvironmentName TeamsGCCHigh -PexipConfiguredConnectorFqdn $PexipConfiguredConnectorFqdn -PexipOutboundFqdn $PexipOutboundFqdn -ExistingVNETResourceId $PxExistingVNETResourceId -UsePrivateRouting $PxUsePrivateRouting
# supply the PFX certificate file password when prompted
# Please enter the password for the PFX certificate '.\xxxxxxxx.pfx': ***************
# Generating the next steps summary (this assumes you are connected to Microsoft Graph and with an authenticated account for use with Azure Resource Manager)
#
# Setting subscription
Set-AzContext -SubscriptionId $PxSubscriptionId
# Getting IP configurations
if ($PxUsePrivateRouting) {
$LB = Get-AzLoadBalancer -ResourceGroupName $PxTeamsConnResourceGroupName
$ExtLB = $LB | Where-Object { $_.Name.EndsWith("-LB") }
$IntLB = $LB | Where-Object { $_.Name.EndsWith("-INTLB") }
$LBExtIPID = $ExtLB.FrontendIpConfigurations[0].PublicIpAddress.id
$LBIntIP = $IntLB.FrontendIpConfigurations[0].PrivateIpAddress
$PublicIPAddresses = Get-AzPublicIpAddress -ResourceGroupName $PxTeamsConnStaticResourceGroupName
$ConnectorPublicIP = $PublicIPAddresses | Where-Object Id -eq $LBExtIPID
$publicIpAddress = $ConnectorPublicIP[0].IpAddress
$privateIpAddress = $LBIntIP
} else {
$LB = (Get-AzLoadBalancer -ResourceGroupName $PxTeamsConnResourceGroupName)[0]
$LBPublicIPID = $LB.FrontendIpConfigurations[0].PublicIpAddress.id
$PublicIPAddresses = Get-AzPublicIpAddress -ResourceGroupName $PxTeamsConnStaticResourceGroupName
$ConnectorPublicIP = $PublicIPAddresses | Where-Object Id -eq $LBPublicIPID
$publicIpAddress = $ConnectorPublicIP[0].IpAddress
}
# Getting connection string for the newly deployed Event hub
$eventHub = (Get-AzResource -ResourceGroupName $PxTeamsConnStaticResourceGroupName -ResourceType Microsoft.EventHub/namespaces)[0]
$eventHubKey = Get-AzEventHubKey -Name "pexip_teams_connector_access" -NamespaceName $eventHub.Name -ResourceGroupName $eventHub.ResourceGroupName
# Printing next steps
Write-Host
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host "When the Teams Connector is deployed, you have to create a DNS A record for your hostname,"
Write-Host "then the Office 365 admin must consent for the CVI App Id to join Teams Meetings"
Write-Host
Write-Host "1) Set up a public DNS A record for $($PxTeamsConnFqdn) pointing to the Public IP of "
Write-Host " the load balancer ($($publicIpAddress))"
Write-Host
Write-Host "2) Give consent to the CVI app. Go to: $AdminConsentUrl"
Write-Host
Write-Host " If Management Consent Source Address prefixes are defined, the administrator"
Write-Host " doing consent must come from one of these addresses (or subnets)."
Write-Host " Consent address prefixes: $($PxConsentSourceAddressPrefixes)"
Write-Host
Write-Host "3) Update the Management Node setting 'Azure Event Hub connection string' for $($PxTeamsConnFqdn) to:"
Write-Host " $($eventHubKey.PrimaryConnectionString)"
Write-Host
if ($PxUsePrivateRouting) {
Write-Host "4) Set up a private DNS A record for $($PxTeamsConnFqdn) pointing to the (private) frontend IP of "
Write-Host " the internal load balancer ($($privateIpAddress))"
Write-Host " See: https://docs.pexip.com/admin/teams_routing.htm#enabling"
}
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-HostAfter deploying the (first) Teams Connector
-
When the script ran, it generated some output that listed the CVI App ID and credentials, similar to this:
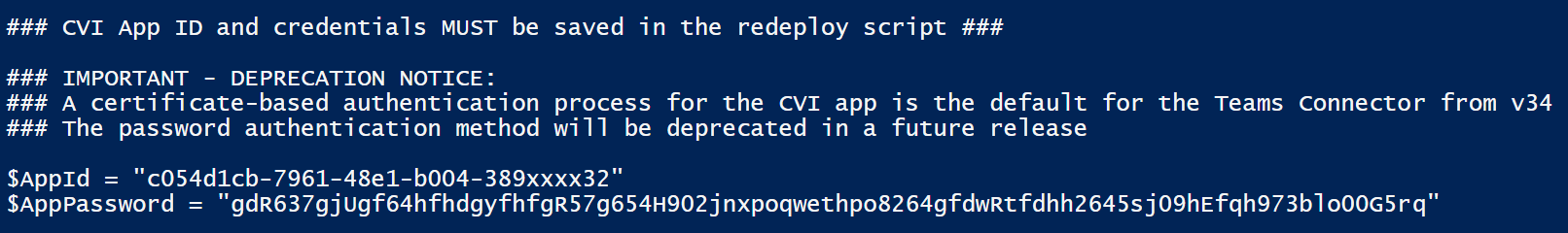
-
Copy the two output lines that define the CVI App ID and password and paste them into a copy of the password-based redeploy script (below), replacing the existing lines that say:
$AppId = ""
$AppPassword = ""This means that if you need to run the redeploy script, you will not rerun the commands that imported the PowerShell module and created the app. Instead you will set the variables to the ID and password of the CVI app that you created the first time.
-
Make sure you save your edited version of the redeploy script in a safe place, as it will be needed when upgrading, or if you need to redeploy, or deploy in another region.
It is critical that you update and store the redeploy script with the CVI app ID and password to ensure that upgrades/redeploys can be done using the same CVI app ID. (Note that the App ID for the API app is a separate ID and is stored in the variable initialization script.)
You can now follow the rest of the standard installation processes.
Upgrading or redeploying a Teams Connector that is still using password-based authentication
You can follow most of the standard steps for upgrading and redeploying the Teams Connector. However, there are some small variations to the process and scripts as described below.
Check Teams Connector software, retrieve your original scripts, and check your Azure environment
When extracting the software and retrieving your scripts, you should:
- Ignore step 4: Add your PFX certificate for the Teams Connector CVI app to this folder — this only applies to CBA.
-
In step 7: use this version of the redeploy script (below) and update it with your Pexip CVI App ID and credentials ($AppPassword) from your previously saved copy (in the CBA version of the script you assign an $AppCertificatePath variable):
-
When your password-based authentication installation script ran, it generated some output that listed the CVI App ID and credentials, similar to this:

-
These output lines should be used to replace the two existing lines in the redeploy script that say:
$AppId = ""
$AppPassword = ""
-
In this section you must use the version of the redeploy script as provided below, which uses a password to authenticate the Teams Connector CVI application towards MS Graph.
This is the redeploy script. It is a variation on the installation script that only performs the necessary commands to redeploy the Teams Connector. As with the initial installation, we recommend running each group of commands step-by-step within PowerShell.
This script applies to software version 39. If you are using an earlier version you should refer to our previous documentation.
- Standard deployment
- High-security deployment (typically Azure GCC High / US Government)
# Ensure the correct script and software combination is being used
try {$PxConnMajorVersion = (Get-Content .\version.json -ErrorAction Stop | Out-String | ConvertFrom-Json).major} catch {Write-Warning "Can't find version.json file. Make sure you run the installation script from the folder into which you extracted the files from the Teams Connector ZIP"}
if ($PxConnMajorVersion -ne "39"){Write-Warning "The Connector version (extracted ZIP files) and this deployment script version do not match. Connector version = $PxConnMajorVersion. Deployment script version = 39"}
# Connect to PowerShell Azure Resource Manager account
# Set execution policy for the current PowerShell process, when prompted type A (Yes to All)
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process
# The Unblock-File cmdlet lets you run PowerShell script files that were downloaded from the internet.
# By default, these files are blocked to protect the computer from untrusted files.
Get-ChildItem -Recurse | Unblock-File
# Import the PexTeamsCviApplication PowerShell module
Import-Module .\PexTeamsCviApplication.psm1
# Import Az Powershell modules
Import-PexAzurePowershellModules -ErrorAction Stop
# Import Microsoft.Graph Powershell modules
Import-PexMicrosoftGraphPowershellModules -ErrorAction Stop
# Connect to Azure with an authenticated account for use with Azure Resource Manager (in same window to reuse variables)
Connect-AzAccount
# Connect to Graph
Connect-PexTeamsMsGraph
# Before running the following commands, update the following 2 lines/variables with the CVI App ID and password
# that were output when the installation script was run
$AppId = ""
$AppPassword = ""
# Change context to the Pexip Subscription and set the app credentials
Set-AzContext -SubscriptionId $PxSubscriptionId
$AppSecurePassword = ConvertTo-SecureString -AsPlainText $AppPassword -Force
# Virtual Machine Scale Set (VMSS) creation
# Provide credentials to be used as local user/password for Pexip Teams Connector VMs
# Create a password (using the initialization script variables) for the Windows VM
$PxWinAdminSecurePassword = ConvertTo-SecureString -AsPlainText $PxWinAdminPassword -Force
$PxWinAdminCred = New-Object System.Management.Automation.PSCredential -ArgumentList $PxWinAdminUser,$PxWinAdminSecurePassword
# Optionally if you did not want to specify the password as a variable, use Get-Credential
# $PxWinAdminCred = Get-Credential
# Deploy the Teams Connector VMs
# this step can take up to 30 minutes to complete
.\create_vmss_deployment.ps1 -SubscriptionId $PxSubscriptionId -AzureVmSize $PxAzureVmSize -ResourceGroupName $PxTeamsConnResourceGroupName -VmssName "$($PxBaseConnName)$($PxVmssRegion)" -VMAdminCredential $PxWinAdminCred -PfxPath $PxPfxCertFileName -TeamsConnectorFqdn $PxTeamsConnFqdn -PexipFqdns $PxNodeFqdns -instanceCount $PxTeamsConnInstanceCount -AppId $AppId -AppPassword $AppSecurePassword -StaticResourcesResourceGroupName $PxTeamsConnStaticResourceGroupName -IncidentReporting $PxTeamsConnIncidentReporting -RdpSourceAddressPrefixes $PxMgmtSrcAddrPrefixes -PexipSourceAddressPrefixes $PxNodesSourceAddressPrefixes -WupdScheduledInstallDay $PxWupdScheduledInstallDay -WupdScheduledInstallTime $PxWupdScheduledInstallTime -WupdActiveHoursStart $PxWupdActiveHoursStart -WupdActiveHoursEnd $PxWupdActiveHoursEnd -CustomerUsageAttribution $PxCustomerUsageAttribution -UseAzureHybridBenefit $PxUseAzureHybridBenefit -Tag $tags -TeamsConnectorApiApplicationId $TeamsConnectorApiApplicationId -FunctionsDedicatedHostingPlan $FunctionsDedicatedHostingPlan -EventHubSourceAddressPrefixes $EventHubSourceAddressPrefixes -VnetIntegration $VnetIntegration -PexipConfiguredConnectorFqdn $PexipConfiguredConnectorFqdn -PexipOutboundFqdn $PexipOutboundFqdn -ExistingVNETResourceId $PxExistingVNETResourceId -UsePrivateRouting $PxUsePrivateRouting
# supply the PFX certificate file password when prompted
# Please enter the password for the PFX certificate '.\xxxxxxxx.pfx': ***************
# Printing finished message
Write-Host
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host " All steps completed."
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host# This script applies to high-security deployments (typically Azure GCC High / US Government)
# Ensure the correct script and software combination is being used
try {$PxConnMajorVersion = (Get-Content .\version.json -ErrorAction Stop | Out-String | ConvertFrom-Json).major} catch {Write-Warning "Can't find version.json file. Make sure you run the installation script from the folder into which you extracted the files from the Teams Connector ZIP"}
if ($PxConnMajorVersion -ne "39"){Write-Warning "The Connector version (extracted ZIP files) and this deployment script version do not match. Connector version = $PxConnMajorVersion. Deployment script version = 39"}
# Set VmImage variable to hold the CIS STIG image properties - STIG image is optional but typical
# In a later step in this script you can choose not to use the STIG image
$VmImage = @{
"sku" = "cis-windows-server2022-stig-gen2"
"offer" = "cis-windows-server"
"publisher" = "center-for-internet-security-inc"
"version" = "latest"}
# Connect to PowerShell Azure Resource Manager account
# Set execution policy for the current PowerShell process, when prompted type A (Yes to All)
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process
# The Unblock-File cmdlet lets you run PowerShell script files that were downloaded from the internet.
# By default, these files are blocked to protect the computer from untrusted files.
Get-ChildItem -Recurse | Unblock-File
# Import the PexTeamsCviApplication PowerShell module
Import-Module .\PexTeamsCviApplication.psm1
# Import Az Powershell modules
Import-PexAzurePowershellModules -ErrorAction Stop
# Import Microsoft.Graph Powershell modules
Import-PexMicrosoftGraphPowershellModules -ErrorAction Stop
# Connect to Azure USGovernment with an authenticated account for use with Azure Resource Manager (in same window to reuse variables)
Connect-AzAccount -EnvironmentName AzureUSGovernment
# Connect to Graph
Connect-PexTeamsMsGraph
# Before running the following commands, update the following 2 lines/variables with the CVI App ID and password
# that were output when the installation script was run
$AppId = ""
$AppPassword = ""
# Change context to the Pexip Subscription and set the app credentials
Set-AzContext -SubscriptionId $PxSubscriptionId
$AppSecurePassword = ConvertTo-SecureString -AsPlainText $AppPassword -Force
# Virtual Machine Scale Set (VMSS) creation
# Provide credentials to be used as local user/password for Pexip Teams Connector VMs
# Create a password (using the initialization script variables) for the Windows VM
$PxWinAdminSecurePassword = ConvertTo-SecureString -AsPlainText $PxWinAdminPassword -Force
$PxWinAdminCred = New-Object System.Management.Automation.PSCredential -ArgumentList $PxWinAdminUser,$PxWinAdminSecurePassword
# Optionally if you did not want to specify the password as a variable, use Get-Credential
# $PxWinAdminCred = Get-Credential
# Deploy the Teams Connector VMs
# this step can take up to 30 minutes to complete
# if you are not using a STIG image then remove the following parameter from this command: -VmImage $VmImage
.\create_vmss_deployment.ps1 -SubscriptionId $PxSubscriptionId -AzureVmSize $PxAzureVmSize -ResourceGroupName $PxTeamsConnResourceGroupName -VmssName "$($PxBaseConnName)$($PxVmssRegion)" -VMAdminCredential $PxWinAdminCred -PfxPath $PxPfxCertFileName -TeamsConnectorFqdn $PxTeamsConnFqdn -PexipFqdns $PxNodeFqdns -instanceCount $PxTeamsConnInstanceCount -AppId $AppId -AppPassword $AppSecurePassword -StaticResourcesResourceGroupName $PxTeamsConnStaticResourceGroupName -IncidentReporting $PxTeamsConnIncidentReporting -RdpSourceAddressPrefixes $PxMgmtSrcAddrPrefixes -PexipSourceAddressPrefixes $PxNodesSourceAddressPrefixes -WupdScheduledInstallDay $PxWupdScheduledInstallDay -WupdScheduledInstallTime $PxWupdScheduledInstallTime -WupdActiveHoursStart $PxWupdActiveHoursStart -WupdActiveHoursEnd $PxWupdActiveHoursEnd -CustomerUsageAttribution $PxCustomerUsageAttribution -UseAzureHybridBenefit $PxUseAzureHybridBenefit -Tag $tags -TeamsConnectorApiApplicationId $TeamsConnectorApiApplicationId -FunctionsDedicatedHostingPlan $FunctionsDedicatedHostingPlan -EventHubSourceAddressPrefixes $EventHubSourceAddressPrefixes -VnetIntegration $VnetIntegration -VmImage $VmImage -TeamsEnvironmentName TeamsGCCHigh -PexipConfiguredConnectorFqdn $PexipConfiguredConnectorFqdn -PexipOutboundFqdn $PexipOutboundFqdn -ExistingVNETResourceId $PxExistingVNETResourceId -UsePrivateRouting $PxUsePrivateRouting
# supply the PFX certificate file password when prompted
# Please enter the password for the PFX certificate '.\xxxxxxxx.pfx': ***************
# Printing finished message
Write-Host
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host " All steps completed."
Write-Host
Write-Host "`n--------------------------`n"
Write-Host
Write-Host